There has been a great deal of talk recently in the news and online about Zoom, specifically all of its so called “security issues”. I do not believe Zoom has a security issue per se, the end user has the ability to modify settings that will make the Zoom meeting more secure as I will discuss in the post. Since the onset of the global pandemic, we have seen surge in “Zoom bombing”. This is where people with malicious intent look for in-progress Zoom meetings to join and cause trouble. There are a number of other issues that exist, such as LinkedIn trawling of attendees and contact detail snarfing.
I found six simple steps when playing around with Zoom to ensure that I am securing zoom meeting correctly.
Add a password to all meetings!
When creating a new Zoom meeting, Zoom will automatically enable the “require meeting password” setting and assign a random 6-digit password. I suggest making this password more complex use all 10 digits.
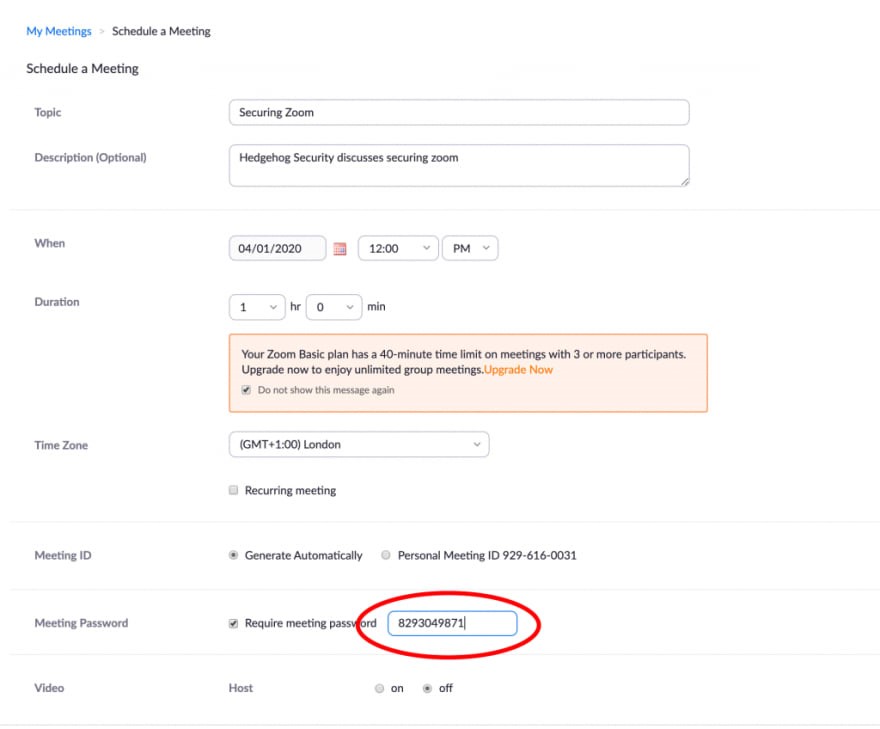
The organization should not uncheck this option as doing so will allow anyone to gain access to their meeting without their permission.
Do NOT share your meeting ID.
Each Zoom user is given a permanent “Personal Meeting ID” that is associated with their account. If the organization gives them their Meeting ID, they will always be able to check if there is a meeting in progress and potentially join if a password is not configured.
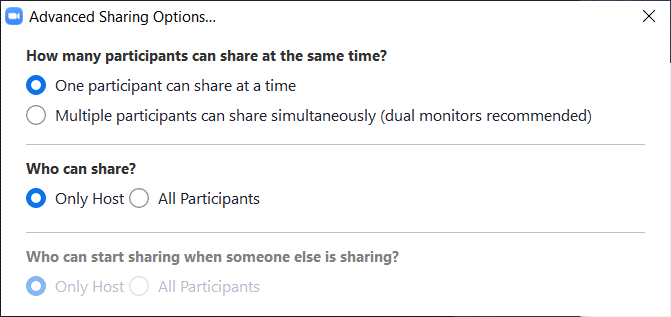
Disable Participant Screen Sharing.
To prevent their meeting from being hijacked by others, you should prevent participants other than the host from sharing their screen. As a host, this can be done in a meeting by clicking on the up arrow next to “Share Screen” in the Zoom toolbar and then clicking on “Advanced Sharing Options” as show below:
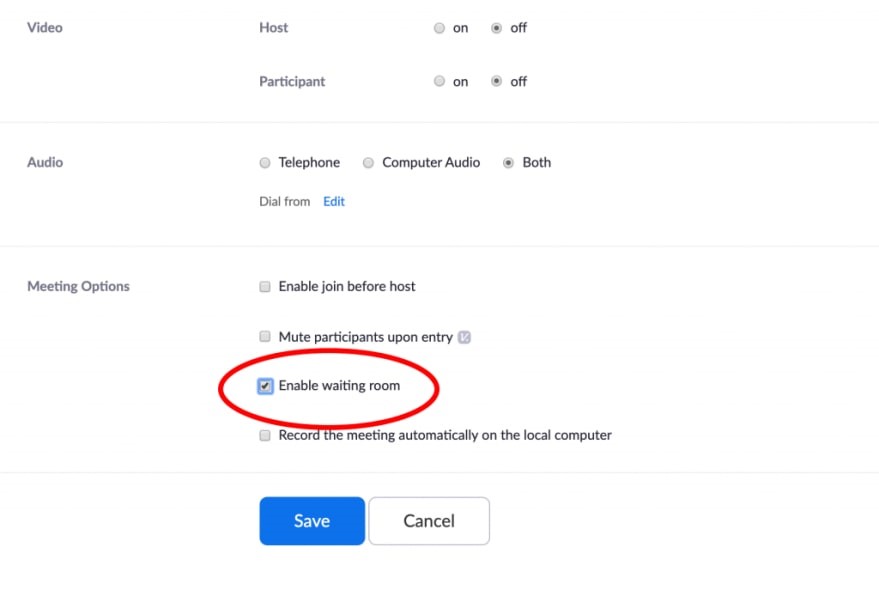
Use waiting rooms.
Zoom allows the host to enable a waiting room feature that prevents users from entering the meeting without first being admitted by the host. This feature can be enabled during the meeting creation by opening advanced settings, checking the “Enabling Waiting Room” setting, and then clicking on the “Save” button.
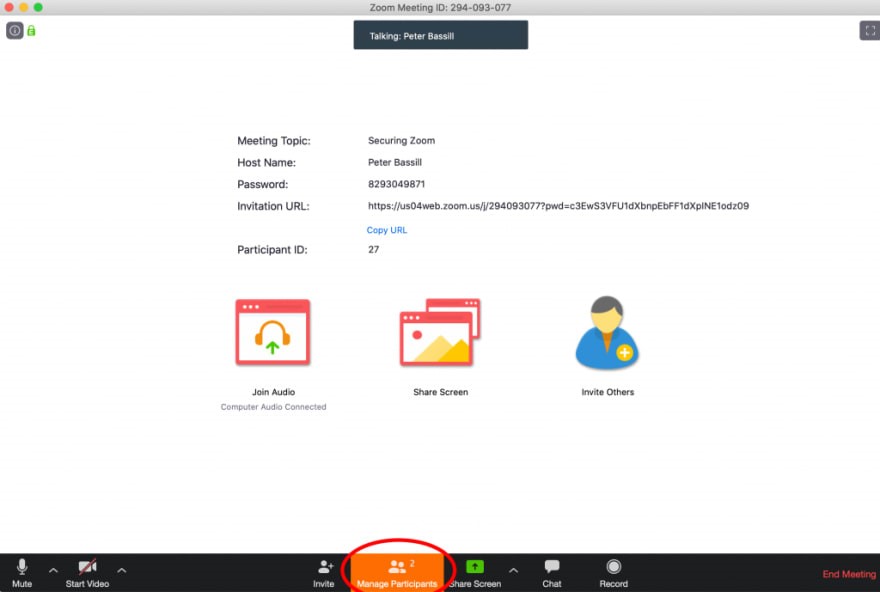
You can then hover your mouse over each waiting user and “Admit” them if they belong in the meeting.
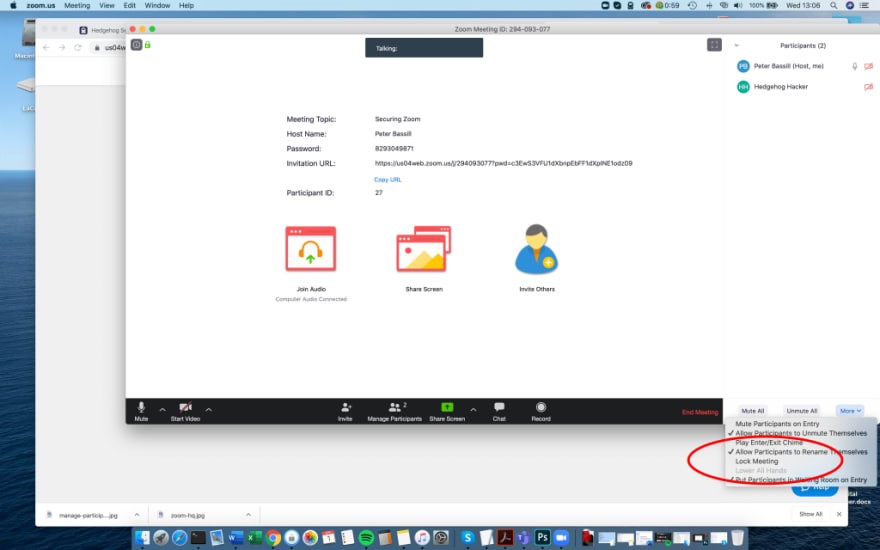
Lock settings when everyone has joined.
If everyone has joined their meeting and they are not inviting anyone else, you should lock the meeting so that nobody else can join.
To do this, click on the “Manage Participants” button on the Zoom toolbar, and select “More” at the bottom of the Participants pane. Then select the “Lock Meeting” option.
Keep Zoom updated.
If you are prompted to update your Zoom client, please install the update.
The latest Zoom updates enable meeting passwords by default and add protection from people scanning for meeting IDs.
With Zoom being so popular at this time, more threat actors will also focus on it to find vulnerabilities. By installing the latest updates as they are released, you and your organization will be protected from any discovered vulnerabilities.
Now Zoom is not the ONLY conferencing software out there. In fact, I would recommend WIRE, FaceTime and WhatsApp, as these three software have end-to-end encryption and when there are conferences when context contains sensitive, classified or confidential information, having end-to-end encryption is vital. You and your organization should also look into your current environment, specifically how data traverses their network, where you have VPN gateways, firewall rules, multi-factor authentication, and network segmentation through Virtual Local Area Networks (VLANs).
Zoom does not have to be the only choice for conferencing software; however if you or your organization chooses it, be mindful of the meeting context and consider implementing these security configurations when creating your next Zoom meeting.